OpenSsl
我们常使用telnet,来探测远程服务器中,某个端口是否是打开的。
我们现在可以使用openssl,来替代telnet
Doc
refer to : https://www.openssl.org/docs/man3.0/man1/
安装
sudo dnf install openssl
openssl version
验证端口访问
refer to : https://www.openssl.org/docs/man3.0/man1/openssl-s_client.html
https://www.openssl.org/docs/man3.0/man1/s_client.html
[root@VM-0-14-opencloudos ~]# openssl s_client -connect 221.181.222.135:8086
CONNECTED(00000003)
140478822508352:error:1408F10B:SSL routines:ssl3_get_record:wrong version number:ssl/record/ssl3_record.c:332:
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 5 bytes and written 289 bytes
Verification: OK
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
可以看到,221.181.222.135的8086端口,是打开的。
下面,我们看一个端口关闭的例子:
[root@VM-0-14-opencloudos ~]# openssl s_client -connect 221.181.222.135:15666
140389772629824:error:0200206F:system library:connect:Connection refused:crypto/bio/b_sock2.c:110:
140389772629824:error:2008A067:BIO routines:BIO_connect:connect error:crypto/bio/b_sock2.c:111:
connect:errno=111
Nmap
refer to: https://nmap.org/book/inst-windows.html
https://zhuanlan.zhihu.com/p/585377081
探测端口
nmap -p 8082 221.181.222.135
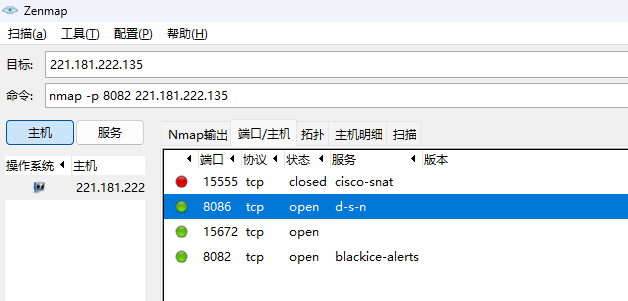
同时探测多个端口:
nmap 192.168.31.180 -p 1-80
nmap 192.168.31.180 -p 80,3389,22,21
nmap 192.168.31.180 -p 1-65535
Netcat
netcat是网络工具中的瑞士军刀,它能通过TCP和UDP在网络中读写数据。
安装:
yum install netcat
# 查看是否安装成功
nc –help
端口扫描的语法
nc [-options] [HostName or IP] [PortNumber]
示例如下:
[root@outgateway ~]# nc -zvw3 192.168.33.15 1883
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Connected to 192.168.33.15:1883.
Ncat: 0 bytes sent, 0 bytes received in 0.01 seconds.
[root@outgateway ~]#
[root@outgateway ~]#
[root@outgateway ~]# nc -zvw3 192.168.33.15 1882
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: No route to host.
命令详解:
nc:即执行的命令主体;
z:零 I/O 模式(被用来扫描);
v:显式地输出;
w3:设置超时时间为 3 秒;